MXDR for Google Cloud

The Basics of Security Tool Management

What is security tool management?
Protecting an organization’s data and infrastructure can have many layers. While most people know about firewalls and passwords, those are only the most basic of protections. Each part of your organization’s technology from web applications and operating systems to servers and networks can be vulnerable to attack and need their own form of protection. This is especially true of today’s hybrid work environments where a single organization can have on-premises, cloud-based, and hybrid technology.
Security tool management is the practice of managing and maintaining all the systems and tools that protect your infrastructure. This can include installing patches and updates, changing configurations to account for new assets or threats, reviewing policies, and more.
7 Layers of Cybersecurity
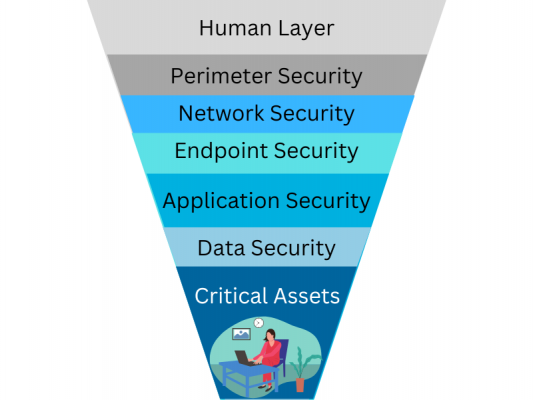
Examples of security tools
Access Control
A report studying data breaches that occurred from March-July 2020 found that more than 40% of all attacks were caused by malicious insiders. While it’s not possible to eliminate all insider attacks, having well managed and maintained access control can help to mitigate the amount of damage a user can do. Access control tools are often administered by your in-house IT staff or MSP partner.
Email security
In 2021, 83% of organizations reported experiencing phishing attacks. Training your employees to recognize and correctly handle phishing attempts is one of the best ways to prevent phishing attacks from being successful, however, having an email security tool is great first-line of defense to prevent malicious emails from ever getting to your inbox in the first place.
Endpoint security
Endpoint security tools are designed to protect individual assets like computers, phones, tablets, servers, and other internet-connected devices. The biggest threat to these devices is ransomware which is becoming more common with ransomware attacks doubling in frequency from 2020 to 2021.
Firewalls
Security information and event management (SIEM)
Why do organizations need security tool management?
Enlisting a partner to help with your security tool management is a great way scale up your cybersecurity without needing to drastically increase your cybersecurity budget or staff. Here are a few of the most common reasons organizations seek out a security tool management partner.
Experienced team at a lower cost
According to a 2022 global survey of business leaders, 60% were struggling to recruit cybersecurity talent while 52% were having difficulty retaining qualified individuals. Skilled and certified cybersecurity professionals can command a high salary in addition to the steep overhead costs of recruiting, hiring, and supporting a full-time employee. This alone can help to justify the cost of hiring an experienced third-party team.
Wide variety of security tool expertise
Increased ROI of existing tools
How does it work?
Working with a third-party security tool management provider often starts with a consultation discussion to understand your current security tool stack. Once you’ve chosen the right partner, they will work with your IT or cybersecurity team to get the access, permissions, and accounts to be able to manage your tools.
One thing to consider before deciding on a partner is whether you are interested in co-managed or fully managed solutions. Co-managed solutions are often the best choice for organizations that have a small in-house team and want to retain control over all aspects of their tools and setups. In this case, the organization and provider will both have access to the security tools and both will actively document any changes made to the systems in an agreed upon location (usually an ITSM CMDB). With a fully-managed solution, the organization will only have read-only access to their security tools and all management/changes will be done by the provider and documented where the customer can see and approve. A top-notch provider will have a clear way to communicate any threat activity they have found, alerts that need to be followed-up on, and also communicate what was done on your behalf.
Finding the right security tool management solution
The simplest way to identify the best fit for your organization almost always comes down to 3 things.
- What the security tool function performs versus the business need. An example would be “I need my emails examined” = Email Content Scanner Solution = A provider that will manage your email content scanner
- The overall “all in” cost of the security solution. This is the cost of the tool itself, any associated licenses, cost to implement, and cost to support/manage
- The security solution needs to be able to connect to, ingest from, or make sense of, the software/data within the organization’s environment
- This seems basic, but is critical to ensuring that the security solution can do the job that the organization needs it to do
Foresite offers security tool management solutions for organizations of all sizes. Our ProVision open XDR platform works with nearly any existing security tool for a seamless integration with real-time dashboards and reporting of your security tool activities. Contact us today to find out more about how you can save time, money, and stress by outsourcing the management of your firewalls and endpoint detection and response tools to us.

