MXDR for Google Cloud

What Every Cyber Security Professional Should Know about Managed Detection and Response
Managing cybersecurity can be a complex task. As organizations expand their digital footprint and become more susceptible to cyber-attacks, they deploy more tools and layers of protection to build a stronger defense. While tools are a good start, they are only as good as the processes and people operating them. Not having the right team to manage and operate those tools is a quick road to making your new purchases just another piece technology no one uses — or as the industry has coined it “shelfware.”
Many mid-size organizations are already operating on limited cybersecurity budgets, and don’t have the additional resources needed to manage or monitor the security tools purchased to protect the business. Managed Detection and Response, or MDR helps solve this problem on many levels. In this blog, we will discuss what MDR is, how it works, and if it’s right for your organization.
What is Managed Detection and Response (MDR)?
Managed detection and response is an outsourced, remote security operation that provides rapid detection, analysis, response, and mitigation of security incidents. It’s a combination of hardware, software, and processes managed by a team of cyber experts operated 24x7x365. MDR is designed to provide organizations with monitoring, detection and response through advanced methods that are not accessible by just buying tools. It utilizes your security tools along with other telemetry and applies advanced analytics and machine learning to correlate threat intelligence information, behavioral anomalies, and previous threats. This process helps to filter out noisy security tool alarms or “false positives” so security teams can focus on real issues and remediate them more rapidly.
A typical cybersecurity hacker can live in an organization’s IT environment undetected for more than 280 days. This is largely due to the high volume of alerts created by security tools that need to be vetted, analyzed, and mitigated by security teams. With Managed Detection and Response, security events are filtered, correlated with other data, and in some cases automatically remediated, making the average time to detect an incident days, if not hours – a massive difference from 280 days.
How Does MDR work?
Managed Detection and Response capitalizes on “Big Data” to achieve economies of scale – the more data, the better an MDR provider can tune your alerts and improve the response to a security event. The core function of MDR includes taking data from different data sources and bringing them together for improved visibility. Some examples of supported MDR datasets include: endpoint devices, cloud, on-premises network, applications, user identity, and data from security tools.
The following is an easy-to-follow step-by-step process to how MDR works:
1.) Data is collected from disparate sources across an organization and brought together under one “data lake.”
2.) The data is then run through a set of advanced analytics that help identify anomalies and connections that security tools may miss to create an “incident.” An incident is not just an alert in this case, but a combination of many alerts and data points from logs that have a higher likelihood of being an incident than a single alert or event.
3.) The incident is then correlated with threat intelligence information, or “Indicators of Compromise” (IoCs). Indicators can include commonly used infrastructure, malware, or even behaviors used by hackers that are collected from various other organizations and shared in a library.
SIDE NOTE: Foresite correlates its incidents with over 70 threat intelligence data sets to ensure the most up-to-date information is available on all investigations.
4.) If the MDR technology believes the data meets the threshold for an incident, only then does an investigation begin to take place.
5.) As this technology does its job of detecting threats, a team of experts operates 24×7 to manage and respond to these incidents, continuously tuning the engines and updating the automated processes and playbooks in place to manage them without needing to scale your team.
6.) If the incident is deemed to be real, or a “true positive,” then it will either be contained or mitigated. This can happen automatically if your organization has the right technologies in place to automate the response, or it can happen with the support of the expert team providing the MDR services.
7.) Since the automated alerts are filtering out “noisy” alarms, the MDR team of experts now also have more bandwidth to “hunt” for potential threats that have gone unnoticed within your environment. This includes building, developing, and deploying new analytics that have high efficacy rates and align to hacker methodologies.
Foresite aligns its MDR analytics to the MITRE ATT&CK with coverage of 712+ common hacker tactics, techniques, and sub-techniques.
Managed Detection and Response & Adjacent Services
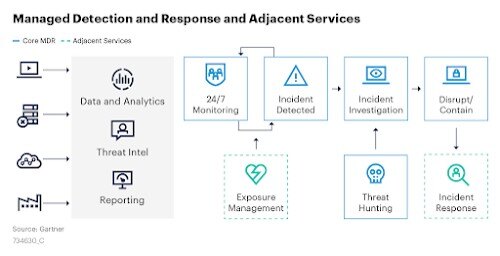
What about Exposure Management and Incident Response?
Exposure management is a critical component of cybersecurity, but not a core function of Managed Detection and Response. It does, however, help to decrease the potential attack surface by identifying the key areas your company that may be at risk for an attack and patching/mitigating as a preventative measure. If exposure management is an option, it’s highly recommended that you incorporate it.
While exposure management is a strong proactive approach, incident response is also a crucial reactive piece to your cybersecurity plan. Having a team of qualified individuals on retainer to quickly investigate and help remediate an incident could be the difference between business being down for a few hours or weeks to months — which typically comes at a high cost to the organization.
Is A Managed Detection and Response Solution Right For My Organization?
The simple answer is — YES. MDR can easily be a good fit for a small, mid-size, or large enterprise business at any point in their security journey. An MDR solution may be critical to your organization if:
- You hold critical customer data that is protected under federal or state law.
- You have remote workers that are not protected by perimeter devices in a network.
- You have a complex IT environment that consists of endpoints, databases, cloud infrastructure, and/or on-premises servers – and no one is monitoring them 24×7.
- You must abide by specific compliance requirements (HIPAA, SOC2, ISO27001, etc.) that require “continuous detection and monitoring” as a control for reaching compliance.
- You have a security team, but they cannot support 24×7 – the MDR provider is then used to augment current operations.


