MXDR for Google Cloud

The Role of SOAR in Modern Security Operations | Google SecOps Explained
This is where a modern platform like Google SecOps SOAR (Security Orchestration, Automation, and Response) becomes a transformative force. By automating the mundane and orchestrating complex workflows, it empowers analysts, hardens security posture, and directly counteracts the root causes of burnout.
What is Google SecOps SOAR?
Before diving into the "how," it's important to understand the platform. Google SecOps is a unified security operations platform that combines the power of a Security Information and Event Management (SIEM) tool—Chronicle—with an advanced SOAR capability.
The workflow begins in Chronicle, where logs from countless sources across an organization are ingested and normalized into the Unified Data Model (UDM). Detections, often written using Yara-L, run against this data. When a log event flags one of these rules, an alert is generated, which in turn automatically creates a case on the SOAR side. This seamless integration is the starting point for all automation, but the raw data itself is often just a collection of logs, IP addresses, domains, and hashes—not yet actionable intelligence. This is where the SOAR workflow truly begins.
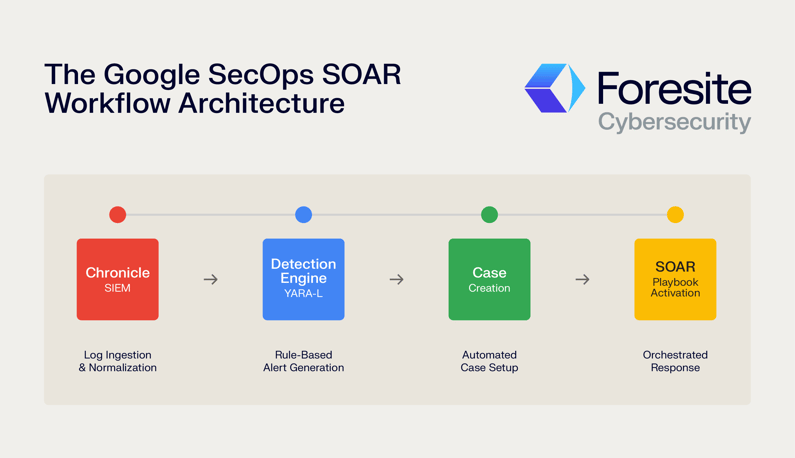
The Google SecOps SOAR Workflow Architecture
From Raw Data to Actionable Intelligence: The Enrichment Engine
A freshly created case is like a pile of raw ingredients. It contains valuable components, but an analyst would have to manually sort, clean, and prepare each one to create a coherent picture. SOAR automates this entire "kitchen prep" process through automated enrichment. When a case is created, a playbook can orchestrate a symphony of actions in minutes:
-
Internal and Historical Context: The first step is to look inward. The playbook automatically searches for past cases (both open and closed) involving the same entities (IPs, domains, users) or detection rules, providing immediate context on whether this is a recurring issue.
-
Deep SIEM Integration: The SOAR platform queries Chronicle to enrich entities and pull detailed information about the detection rule that triggered the alert, providing a deeper understanding of the initial event.
-
Third-Party Threat Intelligence: The playbook then reaches out to a vast marketplace of integrated tools to enrich every entity. This includes platforms like Google Threat Intelligence (GTI), VirusTotal, AbuseIPDB, URLScan, Shodan, API Void, and IP Data. An IP address is checked for malicious reputation, a file hash is analyzed for known malware signatures, and a domain is vetted for phishing associations.
-
The Power of Customization: While the marketplace offers immense out-of-the-box capability, Google SecOps SOAR also features a powerful Integrated Development Environment (IDE). This allows organizations to build custom actions, jobs, and integrations tailored to their unique needs, providing a level of flexibility that goes far beyond a generalized, one-size-fits-all approach.
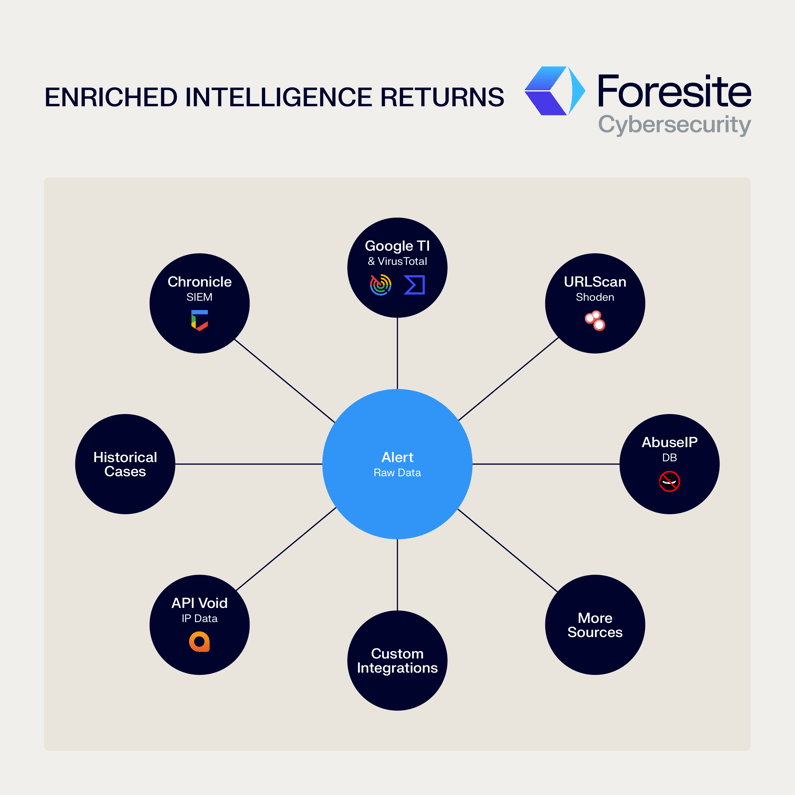
The Enrichment Engine—Automated Intelligence Gathering from Multiple Sources
The Art of the Plate: Effective Reporting and Visualization
Enrichment is only half the battle. Presenting this firehose of new data in a clear, digestible format is just as critical. It’s the difference between being handed a pile of raw ingredients and being served a well-plated meal where each component is distinct and complementary.
Google SecOps SOAR excels at this through its use of dynamic, customizable case views. Instead of forcing an analyst to read through raw JSON outputs, the platform uses HTML-based widgets to display information in a clean, organized manner. For example:
-
A VirusTotal report for a hash is displayed in a formatted table, not a block of text.
-
The enrichment data for an IP address is broken down into clear categories: reputation, geolocation, and recent activity.
-
Quick Actions are presented as buttons directly on the case wall, allowing an analyst to trigger complex workflows—like submitting a detection engineering request—with a single click.
Crucially, this approach normalizes the view regardless of the data source. Whether an alert originates from Cloudflare, Zscaler, CrowdStrike, or SentinelOne, the analyst sees the information presented in a consistent, familiar format, drastically reducing the time it takes to get oriented and start investigating.
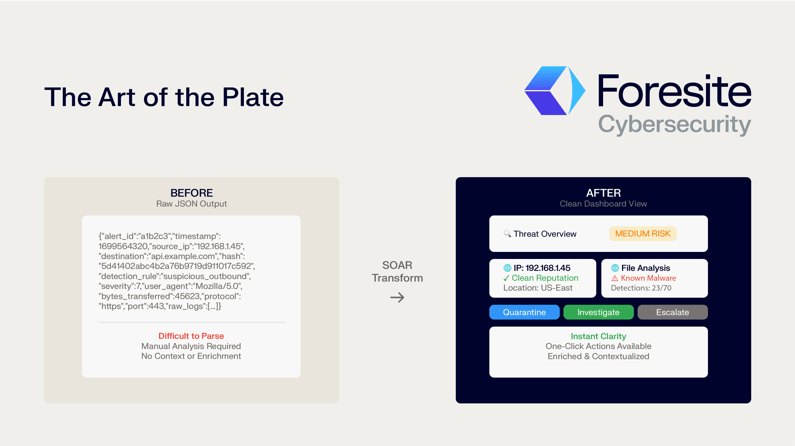
Transformation from Raw JSON to Actionable Dashboard—Radical Transparency in Action
The Journey of Maturity: From Automation to Autonomy
A SOAR platform is not a static tool; it is a living system that evolves with the organization. The workflows you build on day one will look vastly different from what you have on day 364, and that is a sign of a healthy, maturing security program.
This journey typically follows a clear path:
-
Initial Ingestion & Enrichment: The first step is to automate the data gathering and reporting, freeing up analyst time from manual, repetitive tasks.
-
Rule-Based Automation: As the SOC team analyzes case data and communicates with the business, they identify opportunities for more advanced automation. This leads to the creation of rules that can handle alerts without human intervention. For instance, a rule can be created to auto-close known informational alerts or auto-escalate alerts that involve a critical executive’s endpoint.
-
Automated Response: The final stage of maturity involves automated response actions. Based on high-confidence, pre-approved rules, the SOAR platform can take direct action, such as instructing an EDR agent to quarantine a device from the network or blocking a malicious IP address at the firewall. This stage requires significant trust and maturity but represents the ultimate goal of a fully autonomous SOC.
This entire process is a continuous feedback loop. Analysts use the platform, identify areas for improvement, and submit feature requests. The engineering team then enhances the playbooks, which in turn makes the analysts more effective.
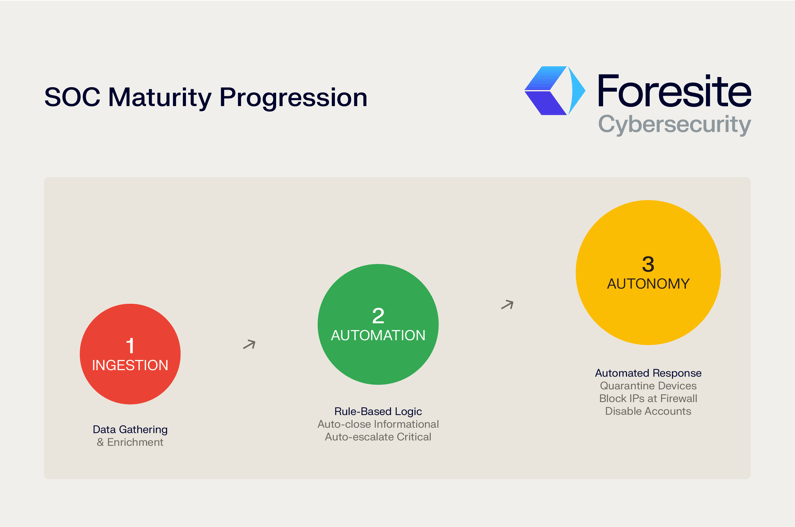
The Three-Stage Maturity Journey—From Manual to Autonomous Operations
The Human-AI Partnership: Supercharging the Analyst
While automation handles the known and repetitive, the next evolution in security operations is the integration of human-driven AI. The goal isn't to replace the analyst, but to create a powerful synergy—an AI co-pilot that supercharges their innate skills. Google SecOps is at the forefront of this shift, embedding powerful AI capabilities directly into the analyst's workflow.
This AI partnership fundamentally changes the nature of the work. Instead of spending hours manually piecing together evidence, an analyst can now leverage AI to:
-
Summarize Complex Cases Instantly: AI can analyze thousands of logs and alerts within a case and generate a simple, natural-language summary of what happened, allowing an analyst to grasp the situation in seconds, not hours.
-
Accelerate Threat Investigation: The AI provides all the necessary information the analyst needs within a single, simple step in the SOAR platform. It acts as a launchpad, presenting a comprehensive overview from which the analyst can choose which entities or events they want to take a deeper look at with further AI-assisted analysis.
-
Receive Guided Recommendations: Based on the context of a case, AI can recommend the next logical investigation steps or even suggest response actions, empowering junior analysts to perform at a near-senior level.
With AI handling the data synthesis and initial analysis, each member of the SOC is freed to focus on the high-impact tasks that require human intuition, creativity, and critical thinking. They can dedicate their time to proactive threat hunting for novel attack patterns, conducting deep threat analysis to understand the adversary's motives, and making the final threat verdict with business context in mind. This elevation of skills doesn't just make the job more rewarding; it dramatically improves the overall service quality and security posture for the client.
Conclusion: Empowering the Analyst, Hardening the Organization
Ultimately, the goal of a platform like Google SecOps SOAR is not to replace human experts but to elevate them. By automating the tedious work of data collection and correlation, it transforms analysts from data sifters into strategic threat hunters. It allows them to focus their skills on complex investigations, proactive defense, and making the critical decisions that protect the organization.
By tackling alert fatigue and analyst burnout head-on, SOAR doesn't just improve metrics—it builds a more resilient, effective, and sustainable Security Operations Center.
Ready to See How SOAR Can Transform Your Operations?
Foresite helps organizations implement and optimize Google SecOps—from automation design to fully managed detection and response—through our Security Operations solutions.
Request more information about Google SecOps with Foresite →
