MXDR for Google Cloud

AI-POWERED, OUTCOME-DRIVEN SECOPS FOR CLOUD & HYBRID ENVIRONMENTS
Make Google Part of Your Security Team
Foresite delivers 24/7 detection, response, and compliance—powered by Google Cloud and operationalized by experts.











WITH POWER THEME YOU CAN CREATE YOUR WEBSITE IN MINUTES, NOT WEEKS!
Smarter Security for Cloud, Multicloud & Hybrid
Foresite combines deep Google Cloud expertise with multicloud flexibility to deliver faster, outcome-driven security—from risk discovery to continuous defense.
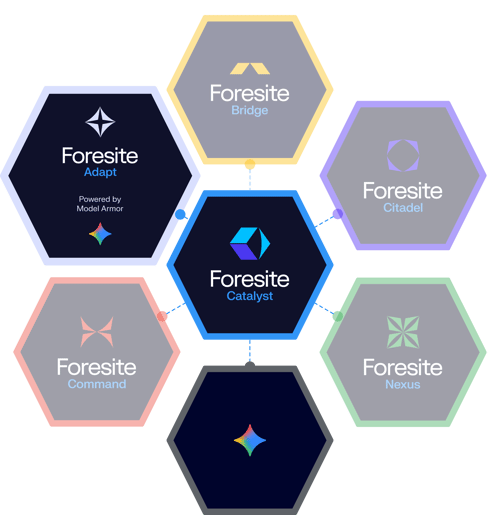
FORESITE PLATFORM MODULES
Flexible, modular, and purpose-built for Google Cloud, Catalyst unifies and automates security operations—delivering seamless protection, continuous compliance, and AI-powered defense at scale.
Get to Know Catalyst.
Customer Retention Rate
Customer Satisfaction Rating
Managed Security Customers
- CATALYST
- BRIDGE
- CITADEL
- NEXUS
- COMMAND
- ADAPT
Foresite Catalyst
THE MODULAR PLATFORM
FOR OPERATIONALIZED SECURITY
Catalyst transforms Google Cloud’s most advanced security technologies into a fully managed, modular security solution—delivering AI-driven protection, continuous monitoring, and automated response without the operational burden.
- Stronger security, without the overhead
- Flexible protection that scales with you
- Seamless security, purpose-built for Google Cloud
Catalyst Bridge
MANAGED GOOGLE SECOPS —
SIMPLIFIED OPERATIONS & RESPONSE
Google Cloud security is complex—Catalyst Bridge makes it seamless. It unifies SecOps, automation, and policy enforcement into one streamlined system, reducing manual work and accelerating response.
- Centralized management across your Google Cloud environment
- Automated detection & response to reduce alert fatigue
- Optional Mandiant Threat Defense for advanced threat investigation
Catalyst Citadel
ALWAYS-ON SECURITY OPERATIONS —
WITHOUT THE IN-HOUSE OVERHEAD
Threats don’t stop—neither should your defenses. Citadel delivers 24/7 Managed XDR with real-time threat detection, AI-powered insights, and named SOC analysts to stop threats before they escalate.
- 24/7 monitoring & rapid response
- Fully managed MXDR—no in-house SOC needed
- Google-powered intelligence to detect attacks earlier
Catalyst Nexus
AUTOMATED SECURITY COMPLIANCE —
STAY AUDIT-READY
Eliminate compliance headaches and stay secure. Nexus automates risk assessments, enforces policies, and ensures continuous alignment with SCCE frameworks and industry frameworks—so you can focus on business, not audits.
- Automated compliance enforcement and real-time monitoring
- SCCE-powered governance and risk management
- Streamlined audits through policy automation
Catalyst Command
REAL-TIME THREAT DETECTION,
FORENSICS & RESPONSE
Cybercriminals move fast—Command moves faster. Powered by Google Threat Intelligence and AI analytics, Command detects zero-day threats, automates response, and accelerates investigation to keep your team ahead of attackers.
- Real-time intelligence to stop attacks before they land
- Automated response to contain threats instantly
- AI-powered forensics to reduce alert fatigue
Catalyst Adapt
AI-DRIVEN DEFENSE, THREAT
DETECTION & MODEL INTEGRITY
AI drives innovation—Adapt ensures it stays secure. Powered by Google's Model Armor, Adapt protects your models from adversarial attacks, manipulation, and data poisoning—without slowing development.
- Prevents adversarial threats targeting AI models
- Secures AI workloads without disrupting innovation
- Built on Google-native AI security
Adaptive Security Model
Enterprise-grade protection — tailored to your reality.
Wherever you are on your cloud security journey, Foresite’s Adaptive Security Model delivers the right services at the right time. Whether you need hands-off Managed Security, expert-led Professional Services, or a combination of both, we’re built to adapt.
- Managed Services
- Profesional Services
Turnkey Managed Security Services
Stop worrying about day-to-day security operations — our SOC becomes your SOC.
Our managed services make Google Cloud part of your security team, delivering 24/7 threat detection, response, and cloud posture management — reducing major incidents by 60% while freeing your internal staff from operational overhead.
-
Managed Detection and Response (MDR)
-
SecOps (including EDR management)
-
Firewall Management
Optimize Every Security Investment
Maximize your security investment with expert guidance and precision testing
Our professional services align your Google Cloud security to both industry best practices and your unique business needs. Whether you need expert architecture reviews, compliance assessments, or precision testing, we ensure every security dollar drives impact.
- SecOps Advisory & Strategy
- vCISO Services
- Penetration Testing
- Breach & Attack Simulation
Smarter Security for Cloud, Multicloud & Hybrid — with Deep Google Expertise
Foresite delivers faster, smarter security outcomes across modern infrastructure — combining Google-native mastery with multicloud flexibility, from risk discovery to continuous defense.
Works with Your Security Stack — Powered by Our Expertise
Modern Cloud Security Platform
Your security foundation, built for modern cloud and hybrid environments.
Google Security Operations
Real-time log ingestion, threat detection, and response at Google scale.
Security Command Centre Enterprise
Continuous compliance and asset posture management across cloud and hybrid.
Mandiant Threat Defense
Curated threat intel from Google’s global research network, directly into MXDR.
Model Armor
AI/ML security — from drift detection to adversarial resilience.
Your Existing Tools
Seamless integration with leading EDR, SIEM, and SOAR platforms.
See How Foresite Delivers
Uncover hidden risks, misconfigurations, and compliance gaps across your assets.
Rapid, expert-led deployment of cloud-native security tools — integrated from day one.
AI-driven threat detection that works across your cloud environments.
SLA-backed incident response to contain threats fast, limit impact, and preserve evidence.
Audit-ready, continuous compliance monitoring and automated evidence collection.
Ongoing tuning, threat intelligence, and security advisory to stay ahead of evolving risks.
Fully managed MXDR, built for modern Cloud
AI-powered detection & rapid response
Continuous compliance & audit-ready reporting
24/7 SOC, backed by SLA-driven response
Threat Dwell Time
faster detection
Faster detection across cloud and hybrid workloads.
Time to Value
faster deployment
Prebuilt integrations mean we’re protecting you faster.
Visibility Coverage
asset visibility
Full asset discovery and telemetry from day one.
Audit-Ready Compliance
continuous evidence collection
Continuous evidence collection with automated compliance.
.
Real-World Results: Foresite in Action

“Foresite’s enablement workshops were top-notch — their team’s knowledge and ability to impart that knowledge was exceptional.”
Linh Vu
Infrastructure Engineer, hMetrix
Ready to Secure Your Cloud — The Right Way?
Talk to the Cloud Security Experts
Whether you’re migrating workloads, securing AI models, or modernizing your SOC, Foresite delivers faster outcomes with deep cloud security expertise.
INSIDE FORESITE'S GOOGLE CLOUD SECURITY JOURNEY
Foresite is among a select group of organizations globally recognized by Google Cloud for its deep expertise in Managed Security Services, Deployment & Integration, and Security Engineering for Google Cloud SecOps.
FORESITE Cybersecurity's VP of Business Development talks about how Google Cloud has become the company's strategic security partner, with products such as Google Security Operations, Mandiant, and Generative AI providing powerful functionality that helps protect FORESITE and its customers.
Join the ranks of forward-thinking agencies leveraging POWER Pro to deliver exceptional results. With unparalleled support and exclusive benefits, it's more than a theme — it's a partnership geared towards your success.


Unlock your company's full potential with a website that not only looks incredible but also delivers measurable results. With POWER Pro, you're not just adopting a theme—you're embracing a tool designed to propel your business forward.



WHAT OUR CUSTOMERS ARE SAYING
Genuine feedback from satisfied POWER Pro users.Intuitive design, seamless functionality, and stellar support
'POWER has completely transformed how we approach website building. Its intuitive design and modular structure allow us to create stunning, professional-looking pages with ease. The flexibility in customization means we can meet every client’s unique needs without breaking a sweat. Regular updates keep the platform fresh and aligned with modern web design trends. And the support? Absolutely top-notch—prompt, friendly, and incredibly knowledgeable.
POWER Theme excels in balancing user-friendly features with robust customization options, including CSS overrides for advanced users. Whether you're new to website building or a seasoned pro, it adapts effortlessly to your skill level.'
Intuitive design, seamless functionality, and stellar support
'POWER has completely transformed how we approach website building. Its intuitive design and modular structure allow us to create stunning, professional-looking pages with ease. The flexibility in customization means we can meet every client’s unique needs without breaking a sweat. Regular updates keep the platform fresh and aligned with modern web design trends. And the support? Absolutely top-notch—prompt, friendly, and incredibly knowledgeable.
POWER Theme excels in balancing user-friendly features with robust customization options, including CSS overrides for advanced users. Whether you're new to website building or a seasoned pro, it adapts effortlessly to your skill level.'
Intuitive design, seamless functionality, and stellar support
'POWER has completely transformed how we approach website building. Its intuitive design and modular structure allow us to create stunning, professional-looking pages with ease. The flexibility in customization means we can meet every client’s unique needs without breaking a sweat. Regular updates keep the platform fresh and aligned with modern web design trends. And the support? Absolutely top-notch—prompt, friendly, and incredibly knowledgeable.
POWER Theme excels in balancing user-friendly features with robust customization options, including CSS overrides for advanced users. Whether you're new to website building or a seasoned pro, it adapts effortlessly to your skill level.'
Intuitive design, seamless functionality, and stellar support
'POWER has completely transformed how we approach website building. Its intuitive design and modular structure allow us to create stunning, professional-looking pages with ease. The flexibility in customization means we can meet every client’s unique needs without breaking a sweat. Regular updates keep the platform fresh and aligned with modern web design trends. And the support? Absolutely top-notch—prompt, friendly, and incredibly knowledgeable.
POWER Theme excels in balancing user-friendly features with robust customization options, including CSS overrides for advanced users. Whether you're new to website building or a seasoned pro, it adapts effortlessly to your skill level.'

DISCOVER OUR POWER TEMPLATES




DISCOVER THE TOP FEATURES OF POWER Pro
See What Sets POWER Theme Apart from the Rest


Frequently Asked Questions About the POWER Theme
We often hear these questions from users considering the POWER Theme. Find the answers you need to decide if it's the best choice for your HubSpot website.
Absolutely, the POWER Theme is fully responsive!
Whether your visitors are browsing on a desktop, tablet, or smartphone, they'll enjoy a seamless and engaging experience.
Absolutely, the POWER Theme includes free updates!
When you choose the POWER Theme, you're not just getting a one-time product—you're investing in a continuously evolving tool. We are committed to keeping the POWER Theme up-to-date with the latest features, improvements, and compatibility enhancements, all at no additional cost to you.
We offer free unlimited support via support tickets and 2 hours of free customization!
Our dedicated team provides unlimited support through support tickets, helping you with any questions or issues. Plus, we offer 2 hours of free customization to tailor the theme to your specific needs.
Contact our support here.
Yes, if the different websites are managed within one HubSpot account.
You can use the POWER Theme for multiple websites as long as all the sites are managed within the same HubSpot account.
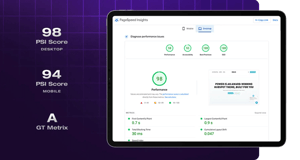
POWER Pro delivers exceptional performance!
Over the years, we've implemented numerous performance optimizations and continuously improve our theme. We're proud to say that the POWER Theme performs exceptionally well compared to other themes in the marketplace, especially considering the extensive features it offers.
Yes, we offer a 7-day free trial!
You can experience the POWER Theme firsthand by accessing one of our demo accounts. This allows you to explore all the features and capabilities before making a commitment.
Reach out to us here, if you want a free trial.
Yes, we offer a 30-day money-back guarantee — no questions asked!
Your satisfaction is our top priority. If you're not completely happy with the POWER Pro theme, simply let us know within 30 days of your purchase, and we'll provide a full refund. No hassle, no hoops to jump through.
Read more about our refund policy here.
Yes, POWER supports multi-language websites!
POWER Pro fully leverages all the multi-language features that HubSpot offers. You can effortlessly create and manage websites in multiple languages, allowing you to connect with a global audience seamlessly.
Yes, you can migrate your website to the POWER Theme!
We offer a paid service to assist you with the migration process, ensuring a smooth transition. Alternatively, we can recommend a partnering agency experienced with POWER to help you migrate your website efficiently.
If you are interested, get a quote here.
Yes, you can use HubDB with POWER!
We offer a specialized solution that allows you to inject HubDB data into our modules without overwriting them. This means you can seamlessly integrate dynamic content into your POWER-themed website. The service is available for $447 per module.
If you are interested, reach out to us here.





